Blog
Novel Phishing Campaign
The scammers are at it again and this time that have developed a new way to get round SPAM filters.
This new phishing campaign uses a damaged Microsoft Word document attachment. As the file is damaged the email filters often cannot read it and pass it through.
Recipients then open the attachment, and Word “helpfully” offers to repair the file. Once repaired, any macros will try to run (this should be disabled by default, but can still happen) or the recipient may be met with a QR code like this:
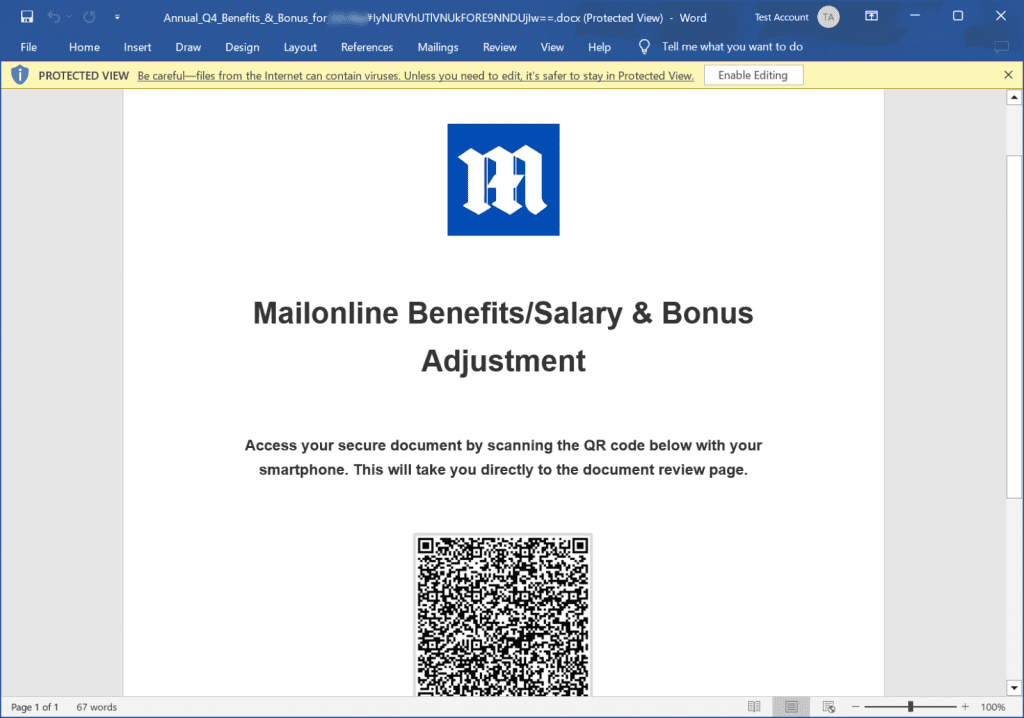
This is particularly tricksy as most of the time you’ll need a phone to scan the QR code. This leaves recipients further at risk as personal devices tend to lack high level protections like antivirus software. 😢
So, what can you do?
- Never open an attachment or link from an email or sender you are not expecting!
- If the sender is known to you but the message is odd or unexpected call them to confirm if it’s genuine – they may have had their account compromised so emailing them won’t really help
- In this example the campaign inserts Base64 encoding schemes into the attachment name (eg: #TEXTNUMRANDOM45==) so look out for this in particular
- Use the reporting buttons in Outlook to report any suspect messages
- If you are a Select Technology customer, this creates a ticket for us to look at and reports the message(s) to Microsoft
- Avoid QR codes: Unless you’re expecting one, steer clear. They can lead you to malicious websites.
Stay safe out there ✌️

Russell Gower-Leech
Cybersecurity Manager at Select Technology, Russ has a huge love for all things security working hard building security into ours and our clients culture.
Latest cybersecurity articles
- Top tips for a safer online experienceIt’s Safer Internet Day – Russell’s favourite day of the year 🙂 It’s a great reminder that staying safe online is everyone’s responsibility – from protecting personal data and passwords to spotting phishing and online scams.
- How to identify AI created content and its cybersecurity implicationsArtificial Intelligence (AI) has transformed content creation, enabling businesses and individuals to produce blogs, images, emails, and social media posts at scale. While this technology offers efficiency and creativity, it also introduces challenges.
- Your team members are helping the hackers!Yes, you read that right. 😲 The biggest threat to your organisation’s cybersecurity might not be a shadowy figure in a hoodie halfway across the world, it could be sitting right next to you in the office.
- Novel Phishing CampaignThe scammers are at it again and this time that have developed a new way to get round SPAM filters.
- Why SMEs need to up their Cybersecurity gameIn an era where cyber threats are evolving at an unprecedented pace, small and medium-sized enterprises (SMEs) in the UK must prioritise robust IT support with integrated cybersecurity elements to safeguard their operations.
- Why should I get Backup for 365?We recommend backing-up your Microsoft 365 data to another cloud-based server, ensuring that if someone does get past the heavy security that we have set up or there are any internal human errors, we can quickly recover your data and make sure that your organisation keeps on running.
- Cyber Security Awareness monthWell it’s officially October which means its Cyber Security Awareness month and I know what you’re thinking “not another piece of sales material disguised as ‘awareness’ banging on about how AI will revolutionise the security of my business” – absolutely not!
- What on earth is NIS2?Another day, another weird tech acronym! This time it’s related to cybersecurity. NIS2 (Network and Information Security version 2) is the latest EU directive that aims to improve the cybersecurity and resilience of organisations that provide particular services.
- Why your business needs Cyber EssentialsYou’d be forgiven for thinking the end is nigh if you follow the news. Every day we see our streams updated with stories about household names being victims of cyber crime or new ‘critical’ vulnerabilities in applications and services.
- Things you didnt know you needed: Computer LockMake sure you don’t get pranked in the office, whenever you leave you laptop or computer at your desk!
- Whats good got to do with it? Security awareness trainingI recently went to the International Cyber Expo (ICE) for the first time and attended a talk by Dr Jason Nurse. The talk was on the study they conducted on the behaviours and attitudes towards Security Awareness Training.
- QR CodesCyber crooks are always on on the look out for new and effective ways to beat security systems and people to steal. There is a growing trend of criminals using QR codes as part of their phishing campaigns, specifically trying to steal Microsoft credentials.
- Microsoft 365 phishing attackThe cyber criminals are at it again! ? They are now using Microsoft’s Rights Management Services (RMS) to steal credentials!
- Hacked, scammed and deleted: A cybersecurity taleThe most tech savvy, security conscience business can be hit by a security breach.Are you prepared?
- Microsoft Outlook vulnerabilityYou may have seen in the news that Microsoft has identified a particularly nasty Outlook vulnerability.
View all cybersecurity articles >