Cyber Essentials: The security MOT
When you drive your car, you can trust that it’s safe because each year you go and get that all important MOT; checking that the tyres are legal, or the lights are working, nothing’s loose and about to fall apart. Guess what?! Cyber Essentials is sort of the same, but for cybersecurity!
So, what is Cyber Essentials?
Cyber Essentials is a Government-backed scheme that sets certain technical expectations/standards that you need to adhere to to pass Cyber Essentials. This provides your organisation a great check list of things that you need to do to make it harder for the “crims” to compromise your business.
A Cyber Essentials certification is becoming a “need to have” requirement as threat levels increase and the continued use of technology grows. For instance if you want to create partnerships or bid on certain contracts (specifically Government), you may find them asking you, “are you Cyber Essentials certified?” and if you are not, then you may be turned away!
What does Cyber Essentials look at?
There are many aspects that Cyber Essentials covers. Some are really easy to control and others are a little bit harder, but not so onerous that it would scare you ?. These are the five basic elements within Cyber Essentials:

Use a firewall
A firewall is an area between your computer/organisations network and the world wide web. Within this area incoming traffic can be analysed to find out whether it should or should not be allowed onto your network. As part of Cyber Essentials you would be required to have this working and protecting your organisation.
Secure your devices and software
New devices and software are often set to be quite “open” by default to allow you to get setup. So it is key to make sure that you dig into the settings and increase the security level, and remove any access or software that is not needed by your organisation.
This might sound “basic”…. but set up passwords across your devices and accounts, ensuring that you implement good passwords! Then to really ramp up the security enable MFA or 2FA, this adds an additional layer of security to your password, making it really hard for criminals to breach your organisation.
Choosing the right MFA solution
Control access to your data
Each person or account within your organisation is a potential access point for the criminals, therefore ensuring that each only has access to software, settings, online devices etc that allow them to perform their role is really important. If privileges are restricted, then if a hacker does somehow manage to get into the account they will likely be frustrated by what they can access.
Protect yourself from viruses and malware
Protecting your organisation from viruses and malware is extremely important. Just like on a home PC, you would purchase anti-virus software and enable for instance, Windows Defender, you should be doing the same for your organisation. Installing software can be a great way to get your device infected – you can protect your organisation by not allowing installation without admin rights, or by creating an “allowed list” that you know are safe.
Viruses and malware are a key tool used by criminals to infect an organisation, corrupting data and in lots of case locking you out of your business, until you pay for it back. There have been many high profile cases of this lately in the news.
Update
Keep your devices and software updated! Updates not only bring great new functionality, but most importantly, new security. This applies to everything, from operating systems, phones to programs and apps. Not updating can mean that a “found” security flaw will not have been secured and will leave your organisation open to risk.
The human factor…
The one caveat that I will include is that Cyber Essentials can’t protect you from the one weakness that technology can’t replace and that’s people. There is, however a way you can mitigate the risk… training, training and more training! Guess what? We provide that too ?.
Our training consists of simulated phishing campaigns that are targeting at catching out your team, not to embarrass them, but to educate them, and that’s what the second part of the training includes.
For example, only a few weeks ago, I got an email that almost caught me out. We have all been talking about working from home, and how that will look and then this falls into my inbox… almost got me!
Find out more about our cybersecurity training.
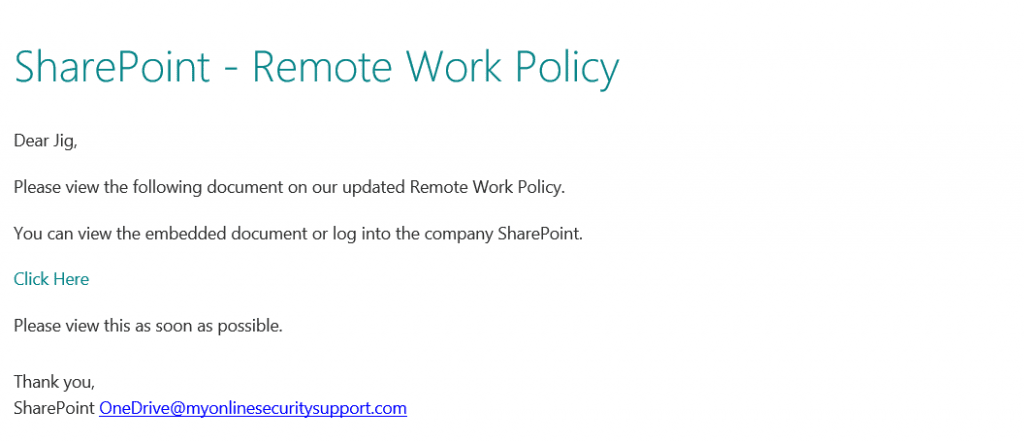
Become Cyber Essentials certified
Protecting your business with Cyber Essentials is the best first step in ensuring that you are protecting you organisation and our crack team are able to help you get there, just give us a call and let’s have a chat.
