How can your business cyber security be strengthened with OSINT?
OSINT is an acronym for Open Source Intelligence. Essentially gathering and using information freely scattered about the interweb. How could this help a business in terms of Cyber Security? It’s a bit of a long story, but like all good stories, we start at the beginning – or at least in this case with a domain
Disclaimer: To make this narrative a bit easier to follow I’ve performed this process on a company picked at random. While all of this information is freely available to anyone who knows how to look I don’t like the idea of handing over a potential treasure map, so I’ve redacted a lot of specific detail. In addition this will not be an exhaustive list; OSINT is a huge topic and there is so much more to talk about, this is just to give you a taste of what’s out there and how it can be used.

Let’s start at the very beginning
Now you could start with just a company name and find their domains with a good old fashioned search engine query (sorry making a concerted effort not to name the big G search engine – unless they’d like to offer sponsorship ?).
What can be discovered about your business?
Once we have our domain we can very quickly find a company’s website and from there basic contact information such as telephone numbers, maybe the odd e-mail address, office locations if they have multiple sites.
So far, so un-exciting.
The next few things we can find are also somewhat standard, but they become a bit more sinister later on. Many businesses like to use their website as a showcase so there will be information about the business owners, management team and/or senior staff. Client testimonials and possibly some case studies on work carried out for those clients. Depending on the business we can also gather some information on who they partner with if they directly supply or recommend third party products and services.
Let’s get technical, technical
We can take a look at the certificate on the website, a lot of businesses have multiple domains for different business units or systems and often use the same website certificate as it’s simpler to manage and reduces cost. This certificate will tell us the name of the issuing body and will reveal any additional domains or subdomains to us and we can then repeat the process thus far to see if there are other websites, more staff members, clients, etc.
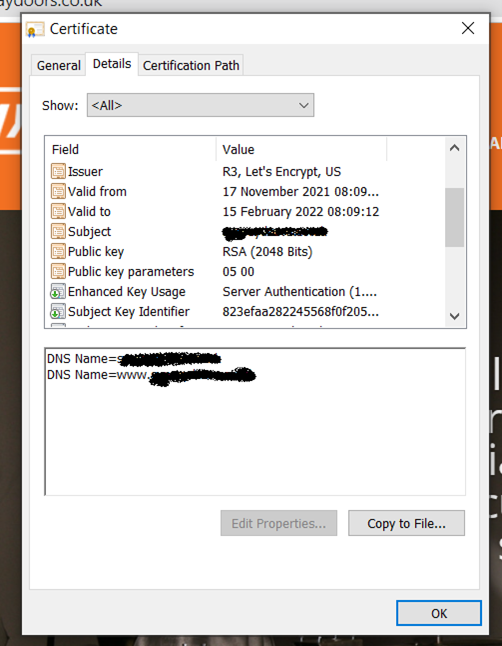
The next thing we can do with these domains is enumerate their DNS entries – for those unfamiliar with this term, DNS is the piece of technology that turns www.select-technology.co.uk into 194.0.252.52 which is the IP (Internet Protocol) address your web browser will use to find and load the web-page. The ‘www’ piece at the beginning, is referred to as a host or subdomain and we can use free tools to find any other sub-domains which may be in place and subsequently any systems which may be at the end of them. Your business will likely have web-based tools or provide remote access to their staff and use a sub-domain like ‘tool.domainname.com’ or ‘vpn.domainname.com’.
The next pieces of interesting DNS are the e-mail records (MX) and SPF (Sender Policy Framework). These are particularly interesting as they tell us who an organisation’s email provider is or if they use any third party email filtering services. These records can also tell us if there are any other IP addresses or domains that are allowed to send emails on the company’s behalf. What you tend to see a lot of here are IP addresses that are or were once linked to internal email systems.
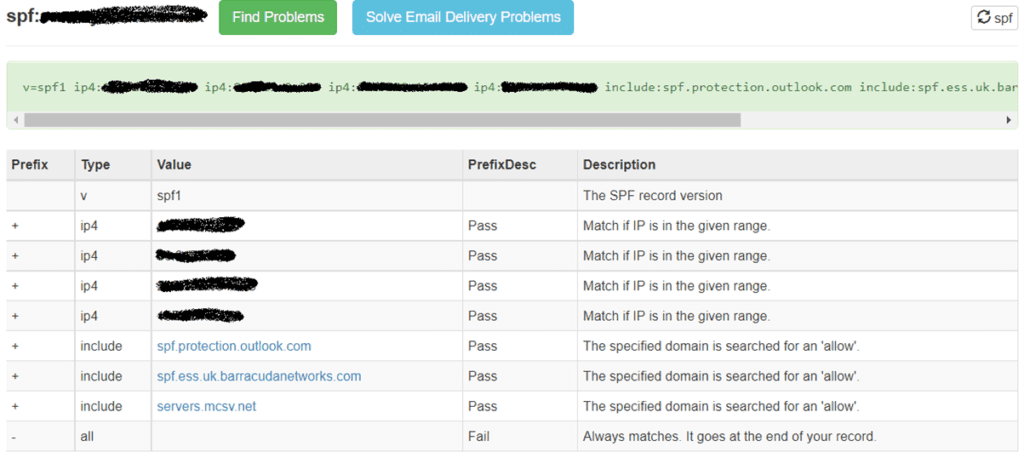
Obviously we can try to work out the DNS record for each of these IP addresses we find or match them to our existing list. If we expand out from there we should have a list of subdomains and IP addresses to go along with them which we can then perform some further look ups to see who they are issued by and where roughly in the world they are. If we see one of the IP addresses is very close to the business’ own address(es) it’s likely this is one of their actual internet connections and we now know which provider they are with.
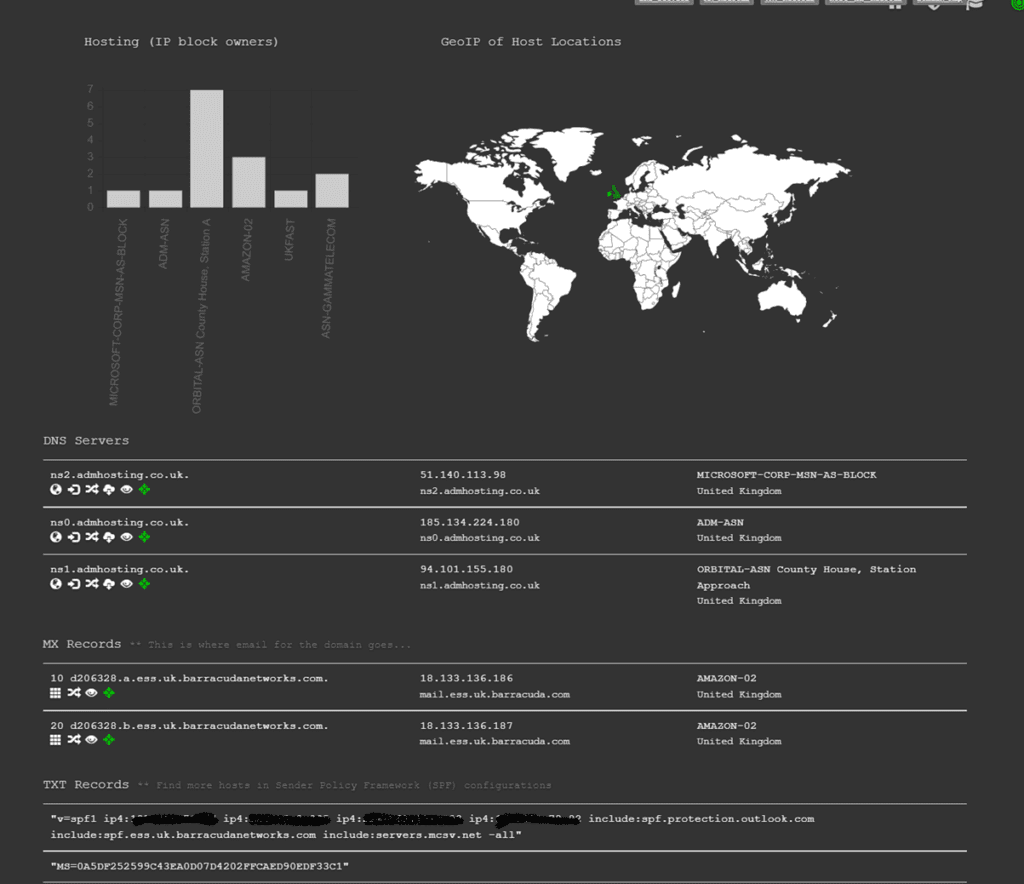
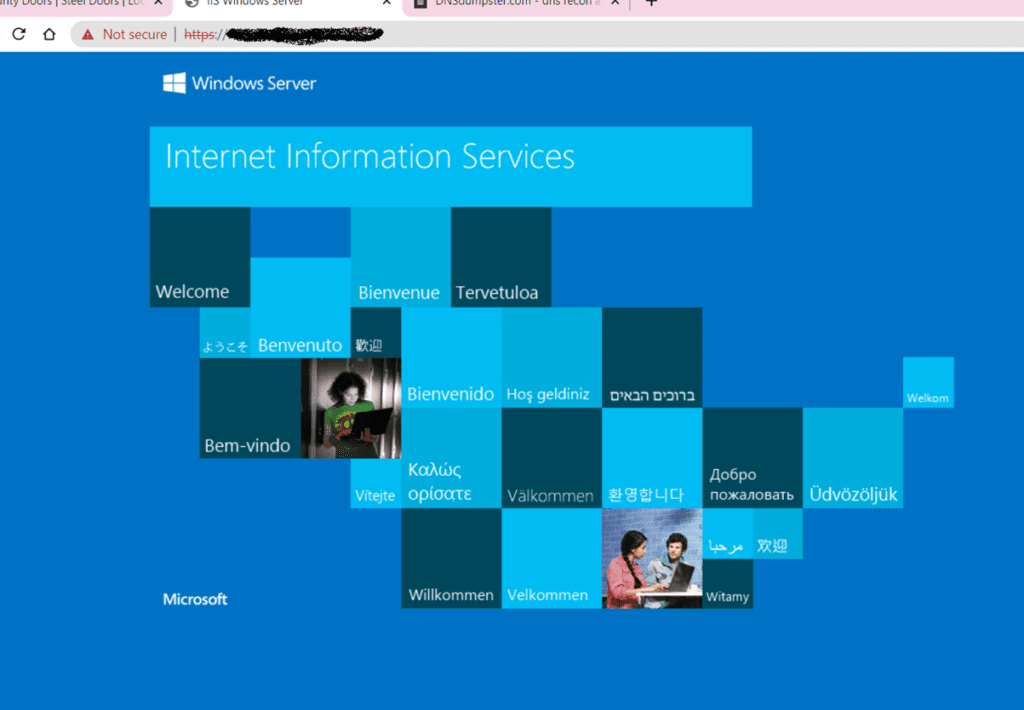
We can take this a step further and see what’s listening at the other end. Taking one record from our example case here we can see a Windows Server. With a little more prodding we could find out the Operating System version and possibly what it’s running. Since we’re talking about OSINT we want to look at passive tools which may have already scraped this information form the server.
Last few quick items then I’ll get to the point, I promise ?
Email addresses
With a quick look up a cyber criminal can get their hands on a list of email addresses based on the company domain name (or at the very least you can get their convention (firstname.lastname@domainname.com for example) that they can then match up with the list of staff names they got from the company’s website. For convenience email address have become user names for most systems.
Social media
Business’ love to shout about the great work they do so their social media feeds can potentially giveaway staff member’s details and customer names.
The darkside
As we’ve talked about before there is a shady part of the internet referred to as the dark web where leaked, lost or stolen credentials are traded or simply shared. With the right tools or contacts criminals may be able to track down some potential credentials for a business based on the domain name. Again these can be matched up to the list of email addresses and staff names from earlier, they may even find a few new ones ?.
So, what does all this mean?
Well by now we should have a reasonable size list of potential targets, be that the business’ own staff or their customers. We also have a list of people and businesses we could try to impersonate. Take the example of knowing which IP is their office’s internet connection. We know who the provider is so we could call up or send an email claiming to be that provider and tell the business that due to an unpaid bill the service is going to cease. Would someone within the business give us payment details like a credit card, or click a link we provide?
Worse still what if we contact that business’ customers posing as one of their staff to “follow up on that piece of work we did” with them.
We’ve also got the other angle of trying to access the business tools with the users and credentials we’ve obtained. Password re-use is a major problem and with so much of our systems being cloud based, it’s very possible that a bad guy could get a foot in the door.
Let’s sum up
Ultimately the point of this exercise is to help businesses understand what information they have shared, consciously, willingly or not so that they can be better prepared in their policies, procedures and staff training. In a number of cases businesses will need to continue to share this information It’s vital for things like email to flow and for them to connect with new customers. In other cases they simply won’t have a choice.
There will however be information they can redact or be more mindful of in the future. In a lot of cases as businesses have moved from in-house IT systems to cloud, they’ve left the records andsystems in place. During an initial transition this can be necessary but after that these should be considered security gaps because as we’ve seen they could help attackers find weaknesses and entry points into your network(s).
Five things your business can do about cyber stalkers
- Think before you share: Stop and think about the information you’re putting out on your website and social media. Avoid naming clients, client staff and your own staff where you do not need to. The whole “meet the team” section of your site may look great from a marketing point of view but the more staff you name along with their hobbies and interests the more targets you give any potential attacker. Try to keep this limited to the directors (as this information can be found easily elsewhere) and the sacrificial sales team (sorry guys).
- Close old systems: Once you’ve migrated systems ensure you close down the old one and remove any records that supported it. Cloud services have the benefit of helping you blend into the crowd and typically have dedicated security teams monitoring activity so get rid of any references to internal systems that no longer need to be there. Additionally consider Access Control restrictions where systems are only accessible from specific connections/locations. This reduces the information that can be obtained and makes penetrating these systems that much harder for attackers.
- User awareness training: Add awareness of this information to your user awareness training. Make sure your staff understand that this information is out there, the common scams the bad guys use and a little of how they think. Your team don’t need to enrol in a criminal psychology degree, bad guys tend to use the same common tactics.
- Update your policies and procedures: Take a look at your policies and procedures and ensure they support the training. Help guide your staff on how to deal with cold callers and ominous emails trying to solicitate information or action.
- Don’t assume: It makes an ass of you and me. ‘This sounds like a lot of work’ or ‘no one would be interested in scamming my business’. Most cyber incidents affect companies of less than 100 staff and you don’t need to be a household name to fall into a criminal’s cross-hairs. We covered this in a recent webinar about why you should care about cybersecurity.
