Microsoft 365 phishing attack
The cyber criminals are at it again! ? They are now using Microsoft’s Rights Management Services (RMS) to steal credentials!
Before we start…
…it would be helpful to understand what RMS is. Essentially, Microsoft’s RMS emails provide a link for users to click to view a message, these are called Restricted Permission Messages (RPMSG). This type of message is great if you need to encrypt messages and send sensitive information and data to someone. The trick with Microsoft’s system is that it doesn’t actually send an email just a link to the message, this means that you would need to login into your Microsoft account to view the message.
How do the cybercriminals get your data?
The way that the criminals are able to get your credentials, is by utilising already compromised Microsoft accounts.
Firstly, an email from one of these accounts asks you to “click to read a message”. This directs you to your Microsoft 365 login page.
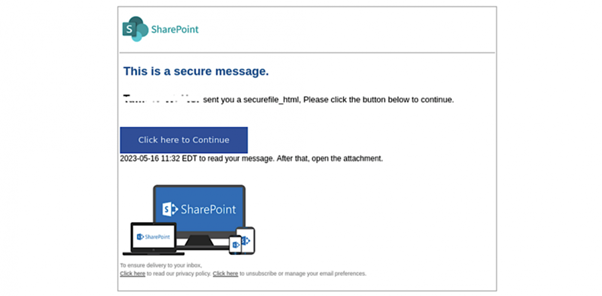
Once you are in, then you are able to see the phishing email to view a fake SharePoint document, often hosted on another legitimate system (Adobe). This includes ANOTHER “click here” action.
This is the final unfortunate event that leads to the crims unleashing their malicious script. The script gathers key system information before sending you to a fake Microsoft login page allowing them to capture usernames and passwords.
Not really a simple click on an email, bing, bang, bosh we have your data!
Why go through this much effort?
This particular phishing process is unfortunately really hard to detect. By using legitimate Microsoft and Adobe services, the low volumes, and the specific targeting, the criminals are able to avoid email security systems and make the emails seem trustworthy. ?
What can you do to protect yourself?
? This and a few checks will always be helpful in protecting you and your organisation. Ask these questions…
- Are you expecting this message?
- Do you know the sender?
- Does the message or replies seem normal?
Answered NO to any of the above! Then you need to check with the sender that this is a genuine message, DON’T click any links, DON’T reply to the message, DO call them directly and DO contact your IT team to check and verify that this is a genuine email. If it’s genuine… all good! If it’s fake… then you are a hero. ?♀️?♂️
We, bang on about this but make sure that you are using Multi Factor Authentication, which is the best way to prevent unauthorised access to your accounts.
The key message is…
If in doubt call you IT team
Want to know more about how to protect your business from the cybercrims? Just get in touch or take a look at WorkSafer our all-in-one business cybersecurity solution.
